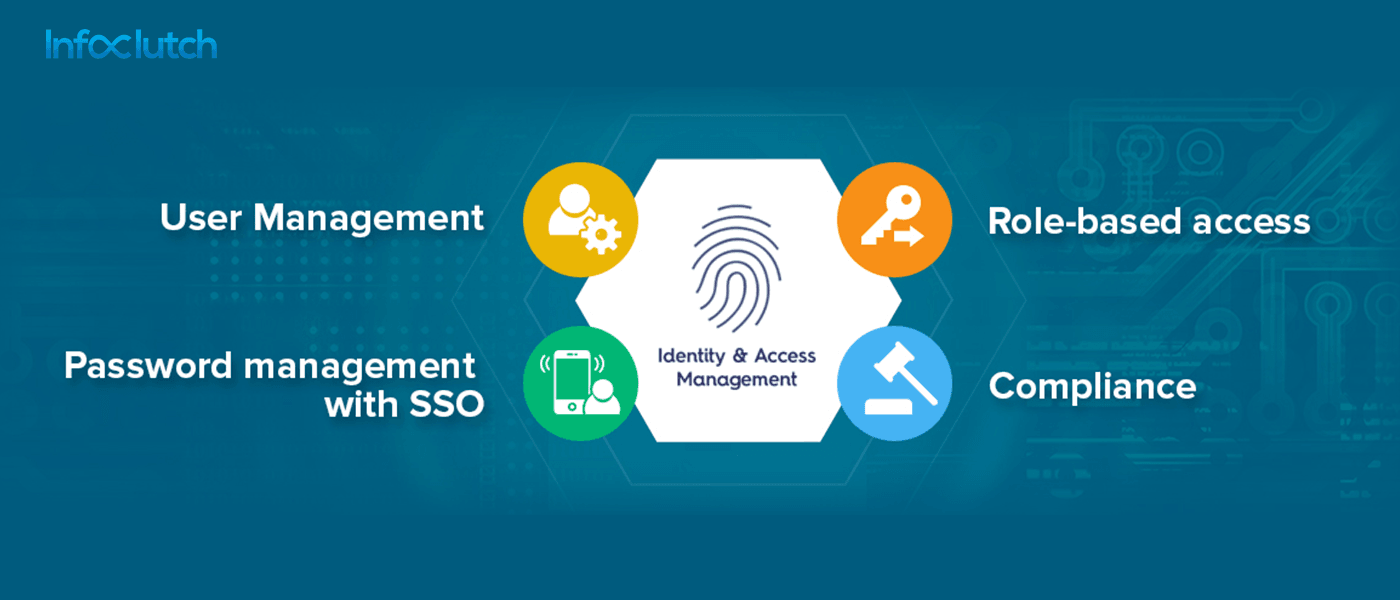
The identity and access management (IAM) is one of the crucial security components for managing security in the organization. It helps the authentic users to access the information and restrict the unauthorized ones for gaining access to the applications and data. An efficient IAM system helps to control and provide the access to the user with ease. The major systems used in the identity access management are the SSO (single sign-on), PAM (Privileged Access Management), and MFA (Multi Factor Authentication).
Almost 64% of the Federal government IT leaders in USA consider IAM as a necessity to address the increasing cyber security threats.
Although IAM might not directly improve the productivity of the employee or the functionality of the organization respectively, but an efficient IAM system surely helps other business and technical process that facilitates in better output and business results.
Some of the basic tools that identity access management has are:
- Password management tools
- Employee data
- Auditing and reporting for the visibility into the systems
- Integrating with the current login systems
- Tools for appending or removing the users
The key aspects of the identity access management are:
- Mobile computing: With most of the organizations adopting bring-your-own-device concept, for giving the users an easy and remote access to the data, mobile computing has become a facilitator in this process. It is accelerating the process and providing the right security to the organization.
The identity access management helps the mobile computing security and activate the mobile devices for using the organization’s resources in the right and effective way. The process to deny access or provide access by IAM, enables the security of the confidential data of the organization. - Helps to prevent the loss of data: Data is the bread and butter of the majority of the organizations. Any loss of data can be a threat to the security of the organization.
DLP (Data loss prevention) is a set of tools for ensuring that the highly sensitive information does not get leaked out and misused by the cyber criminals. The software is driven by PCI-DSS, GDPR, HIPPA. This software, along with the IDA, helps to improve the security of the organization. - Monitoring and reporting: The identity access management helps in the process of monitoring and reporting easily. It keeps track of the login events, real-time alerting of the security system, terminating the session of the user, monitoring every session of the user and duration.
The major benefits of identity access management are:
- Easy access for the users: It helps the users to gain easy access to all systems that are interconnected with each other. The user wherever in the world, can use this information for official work without any hassle. The tech giants are gaining many benefits from this technology, as it provides them the ease to interact with employees, clients, partners, effectively.
- Reduces the IT infrastructural costs: Businesses across the world look for different means in cutting down the costs, IAM helps these organizations by eliminating the investment on the internal help desks. The single sign-on with IAM helps the users to login and access the required information. The IAM effectively executes the identity and authorization management.
- Helps to improve the productivity: The identity access management helps in the automation of the process. The business agility is improved as the employees start performing earlier, thus improving the productivity.
- Helps to achieve the regulatory compliance: The business environment has become challenging, with the ever-changing requirements of the industry. Identity access management is designed to meet these challenges with ease.
- Improves the experience of the user: The single sign-on feature enhances the user experience. With only one user name and password, the user is enabled to access all of the applications that help him to carry out his office work efficiently. Their productivity would not be affected even if they are not working from their office desk as they can use this process from anywhere across the world at any time.
Major challenges with IAM:
- Storage of information at a common place: Implementing the identity access management can be quite risky sometimes as it means you need to store the information at a common place. The information, which includes the credentials if not secured in the right way, might pose serious risk if the cybercriminal attacks and somehow breaks the security of the system.
- Securing the identity on social media: There has been increasing use of social media by organizations to promote their service and increase brand awareness. But when these social identities are attacked and hacked by the cyber criminals, then companies can face obstacles in the process, as the reputation of the brand gets jeopardized. It might also lead to loss of many customers. In such cases, organizations need a reliable identity access management system with the multifactor authentication solutions for alerting the users in case any unauthorized person attempts to login to the system.
Some of the major IAM vendors are:
- Okta
- Microsoft Azure Active Directory
- RSA
- Oracle Identity Cloud Service
Conclusion:
IAM is undeniably an integral security feature that can help organizations in reducing the data thefts, improve the productivity of the employee, reduce operational and IT infrastructural costs, and further optimizing the business results.