WEP or the wired equivalent privacy is the security algorithm. It was introduced in the year 1997.
It is designed for the networks, such as for the IEEE 802.11 wireless networks. The system allows the usage of the 64-bit key or the 128-bit key. It was known as the static key with the help of which the entire traffic data is encoded via the single key.
While it was thought to be an effective solution, in the year 2001, some shortcomings were found in WEP. It was- anybody who is not an authorized user can get into the network and steal confidential information. The static key used here doesn’t change so the cyber criminal could gather enough information for deciphering the data. The key length is also not secure here with the large amount of power used in the current times.
Because of that some more security measures were taken.
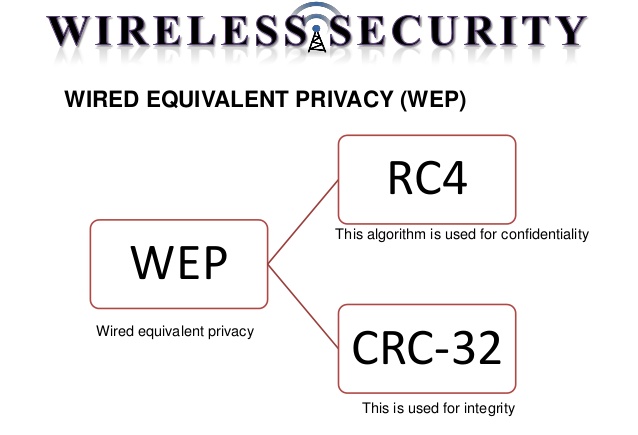
It is recognizable by the key that are 10 or 26 hexadecimal digits. These keys are set up in the router. The major benefit of WEP is that it is easy to deploy on the existing hardware infrastructure. The data privacy is ensured via RC4 or the Rivest Cipher 4. The technology is easy to deploy and configure. The data integrity is provided by CRC-32. The authentication method here is the open system authentication or the shared key authentication.
The most used standards in WEP were WEP-104 and WEP-40. It functions at the physical and the data link layer. The solution was developed to provide the security at the same level as the wired networks.
How does the WEP function?
It uses the data encryption scheme which is the combined form of the system generated key values and the user-generated key values. Whenever, the wi-fi system is deployed, wired equivalent privacy or the WEP decodes the data stream with the help of the discussed keys. The data is made into machine language so that a common person can’t decipher.
The shared keys of the WEP:
The shared keys of WEP are the unicast session key and the multicast key.
The Unicast session key: The key that safeguards the unicast traffic between the wireless client and the wireless AP.
Multicast key: It is the key that safeguards both the multicast and the broadcast traffic in between the wireless clients and the wireless AP.
Advantages of WEP:
- Helps in better key management
- Has good message integrity checking
- Different key is used for every packet
Disadvantages of WEP:
- The major disadvantage of WEP is that it offers no protection against the replay attacks.
- Vulnerable against the Chopchop, Dos attacks and others
- The authentication method of WEP is found to be weak.
It was due to these disadvantages, that users switched over to other technologies such as to WPA2. But some of the wireless routers such as the ASUS ROG Rapture AX11000 Tri-Band wi-fi 6 router are known to using it.

